14) which of the following are breach prevention best practices
Select the best answer. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11.

How To Prevent Data Breaches In 2022 Upguard
Which of the following are.

. Vulnerability assessment is the process intended to identify classify and prioritize security. Properly configure the cloud. All of the above answer a.
Where a breach has taken place companies may need to notify individuals as well as face negative impact on the companys brand and customer loyalty. Companies that leveraged artificial intelligence machine learning. Which of the following are true statements about limited data sets.
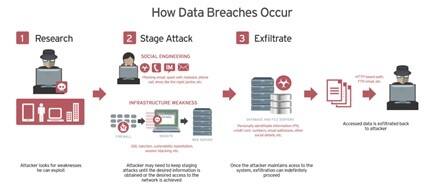
The following are high-level best practices for preventing breaches. Which of the following are breach prevention best practices. However these 30 best practices for preventing a data breach can.
10 The HIPAA Security Rule applies to which of the following. 30 Best Practices for Preventing a Data Breach. Identity sensitive data collected stored transmitted or processes.
All of the above. Which of the following are breach prevention best practices. What of the following are categories.
Train Employees on Security Awareness. In a hyper-connected business world organizational leaders understand that data breaches are a fact of life. Best practices for breach prevent are.
The following are high-level best practices for preventing breaches. Established a national set of standards for the protection of PHI that is created. The employees play an essential responsibility in keeping their.
Logoff or lock your workstation when it is unattended. The typical steps most cybercriminals follow during breach operations are. Invest in security automation.
Identify areas that store transmit collect or process sensitive data. Access only the minimum amount of PHIpersonally identifiable information PII necessary B. 14 which of the following are breach prevention best practicesaccess only the minimum amount of.
Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022. Which of the following are breach prevention best practices. Promptly retrieve documents containing PHIPHI from the.
All of this above. Which are breach prevention best practices. Which Of The Following Are Breach Prevention Best Practices.
In the age of digital data keeping information safe is more important than ever. Which of the following statements about the HIPAA Security Rule are true. Which of the following are breach prevention best practices.
World Bank Board Approves New Fund for Pandemic Prevention Preparedness and Response PPR June 30 2022. WHO intensifies response to looming health crisis in the. Invest in security automation.

Preventing Hipaa Data Breaches Case Studies And Best Practices

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Certificate Management Best Practices Checklist Hashed Out By The Ssl Store

Data Loss Vs Data Leaks What S The Difference Upguard

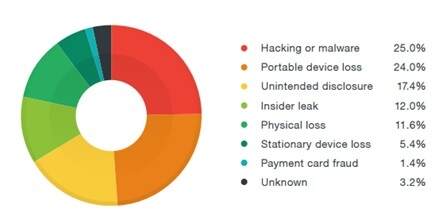
6 Most Common Causes Of Data Leaks In 2022 Upguard

Analyzing Company Reputation After A Data Breach
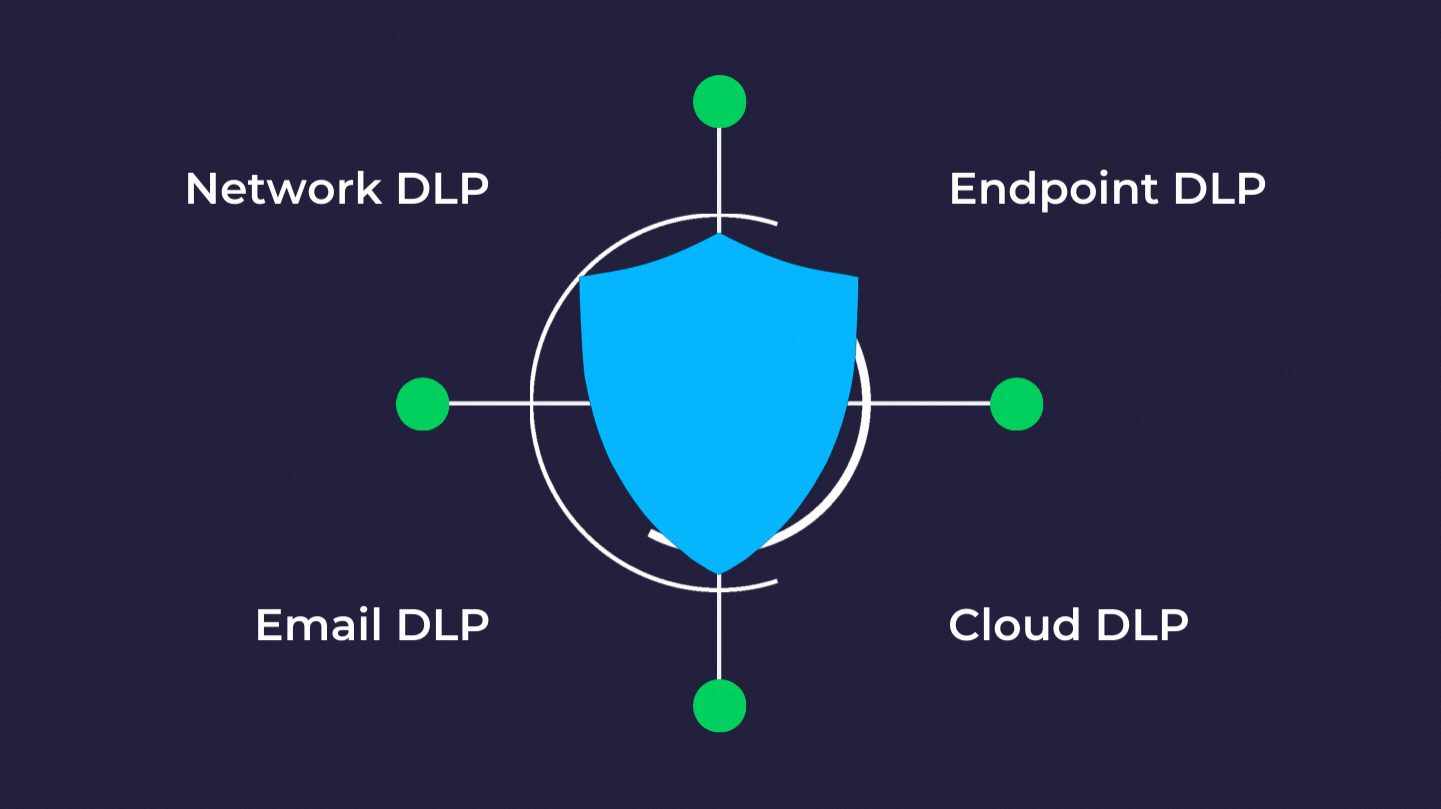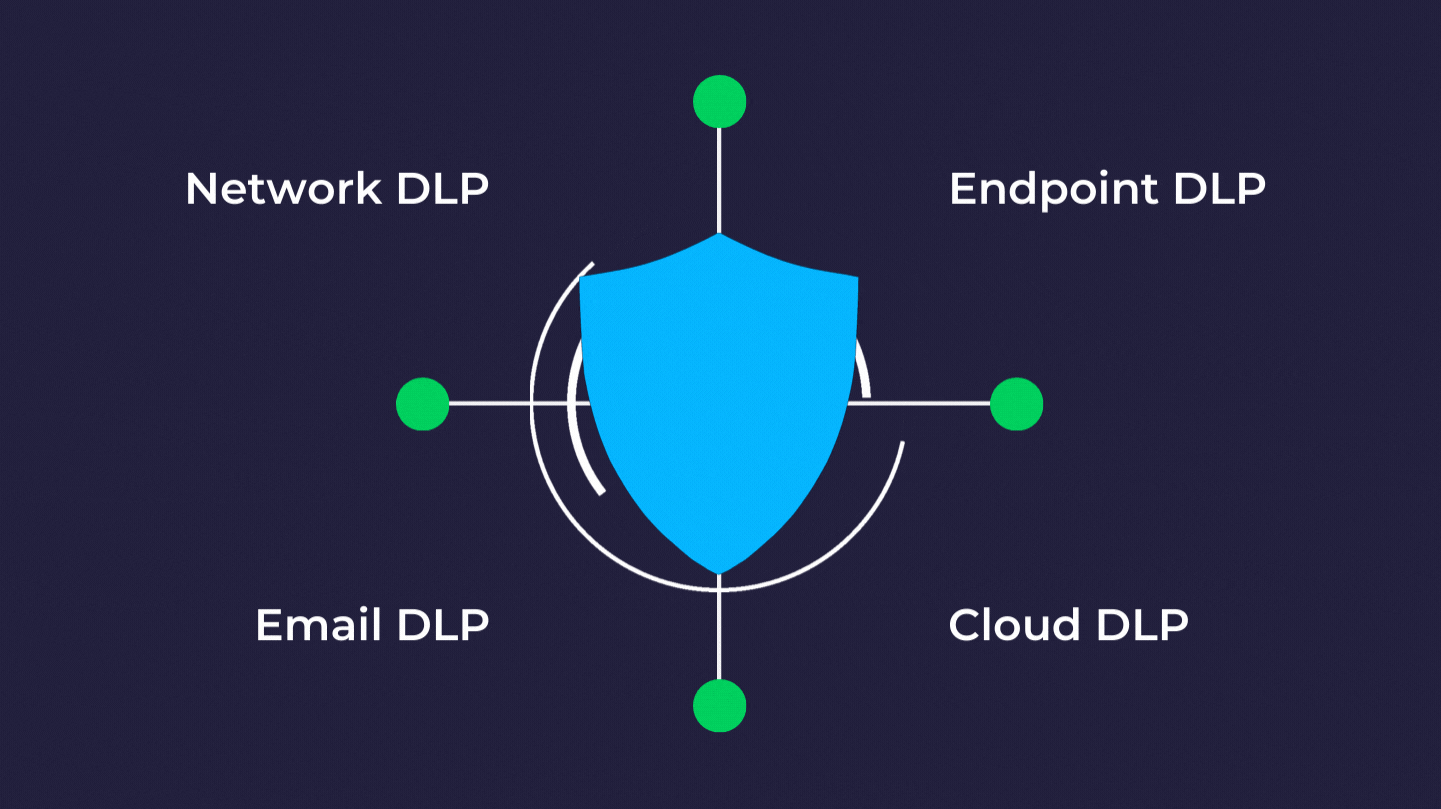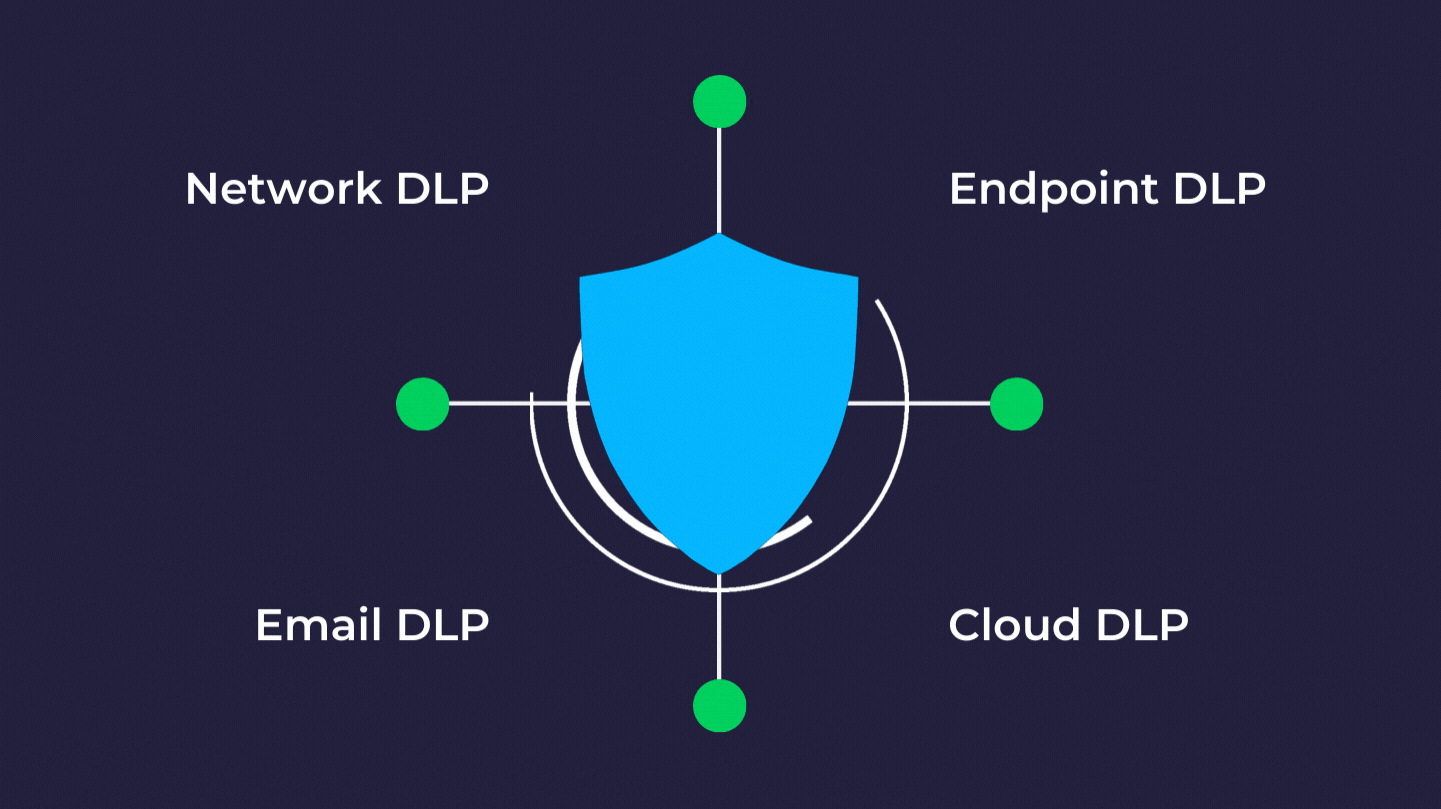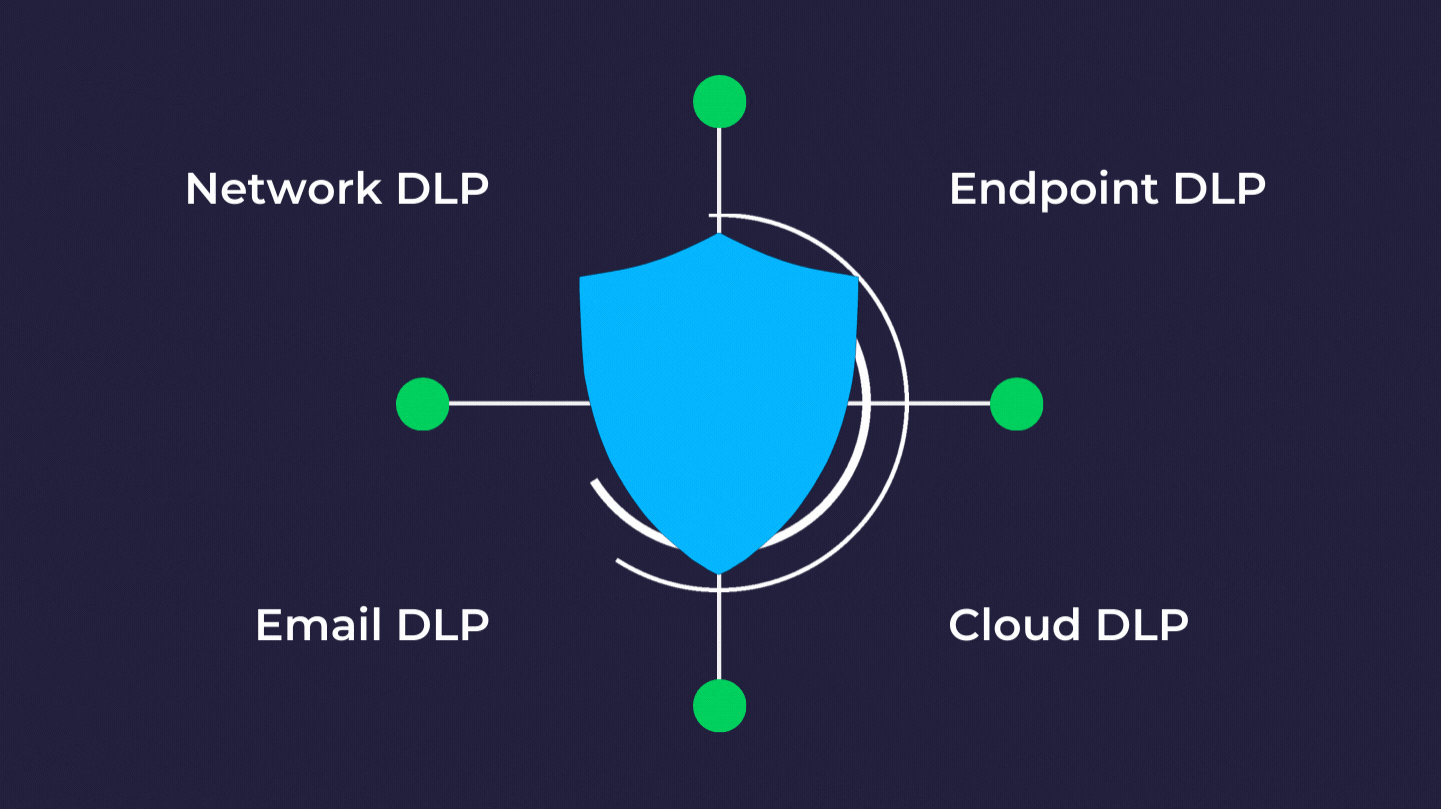
Data Loss Prevention Dlp Everything You Need To Know Strongdm

Data Breach Response 5 Essential Steps To Recovery
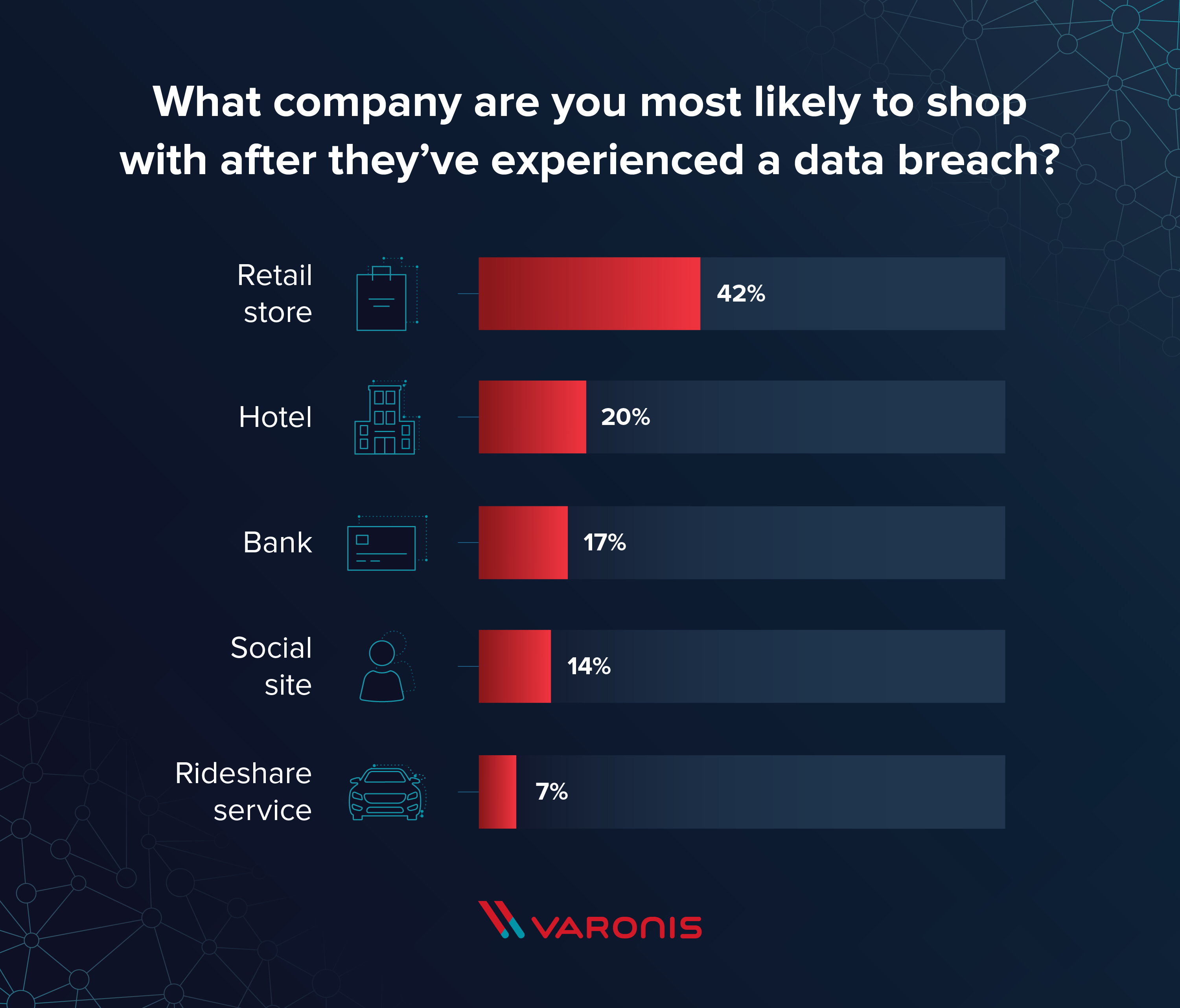
Analyzing Company Reputation After A Data Breach

Analyzing Company Reputation After A Data Breach

6 Most Common Causes Of Data Leaks In 2022 Upguard

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

Top 10 Zero Day Attack Prevention Best Practices 2022 Cybertalk

6 Steps To Developing A Data Breach Response Plan Spectral
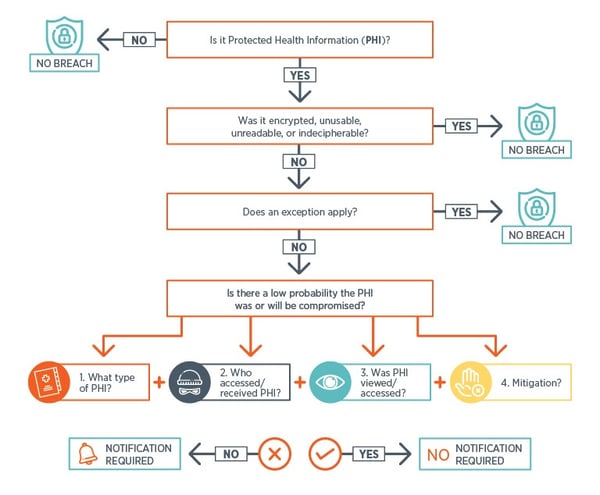
Preventing Hipaa Data Breaches Case Studies And Best Practices
5 Best Practices For Data Breach Prevention Endpoint Protector